Private Tunnel and NetworkManager
Private Tunnel is an OpenVPN-based VPN service provided by OpenVPN Technologies Inc. At some point I signed up for their service and found that while my phone used their Android app without any issues, NetworkManager part on my laptop was not really cooperating.
Eventually I've figured a workaround.
Update: The workaround can be found in Private Tunnel Knowledgebase.
Repeat the steps for the <extra-certs>..</extra-certs> section, and put this content at the end of the file usr.crt you have just saved previously.
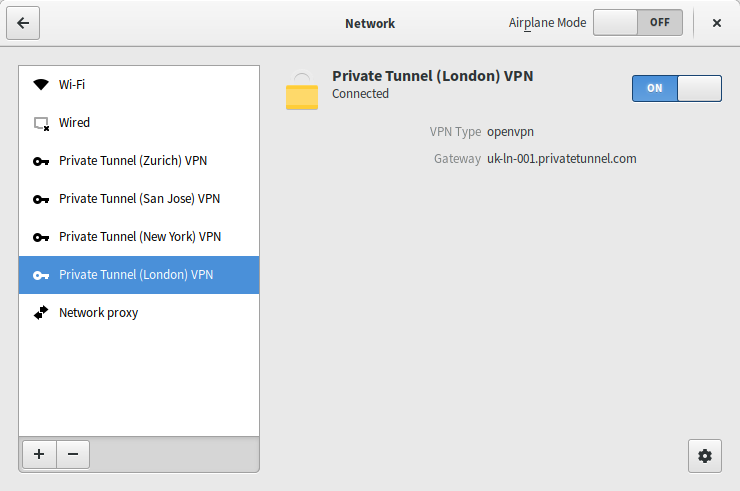
OpenVPN connected via NetworkManager on Fedora 23
NetworkManager does not support .ovpn files that you get from
Private Tunnel, no matter how hard you try.
So, open e.g. San Jose.ovpn downloaded from Private Tunnel and you'll
see:
setenv USERNAME "somebody@example.com" client dev tun remote us-ca-sj-001.privatetunnel.com 1194 udp [...] remote-cert-tls server comp-lzo no auth SHA1 nobind verb 3 sndbuf 0 rcvbuf 0 socket-flags TCP_NODELAY <ca> -----BEGIN CERTIFICATE----- [...] -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- [...] -----END CERTIFICATE----- </ca> <cert> -----BEGIN CERTIFICATE----- [...] -----END CERTIFICATE----- </cert> <extra-certs> -----BEGIN CERTIFICATE----- [...] -----END CERTIFICATE----- </extra-certs> <key> -----BEGIN RSA PRIVATE KEY----- [...] -----END RSA PRIVATE KEY----- </key> key-direction 1 <tls-auth> -----BEGIN OpenVPN Static key V1----- [...] -----END OpenVPN Static key V1----- </tls-auth>
On Fedora, you'll need to extract the contents of the .ovpn file
to pre-defined locations ~/.certs and ~/.pki, as SELinux will
otherwise prevent NetworkManager from reading the files (a feature,
not a bug).
Save the contents between
<ca></ca> to ca.pem, <cert></cert> to
cert.pem, same goes for key and tls-auth.
The trick to get Private Tunnel working with Network Manager is to
add extra-certs data to cert since there is no way to add
extra-certs to OpenVPN command line via NetworkManager.
Afterwards, you will need to reference the files created during OpenVPN setup:
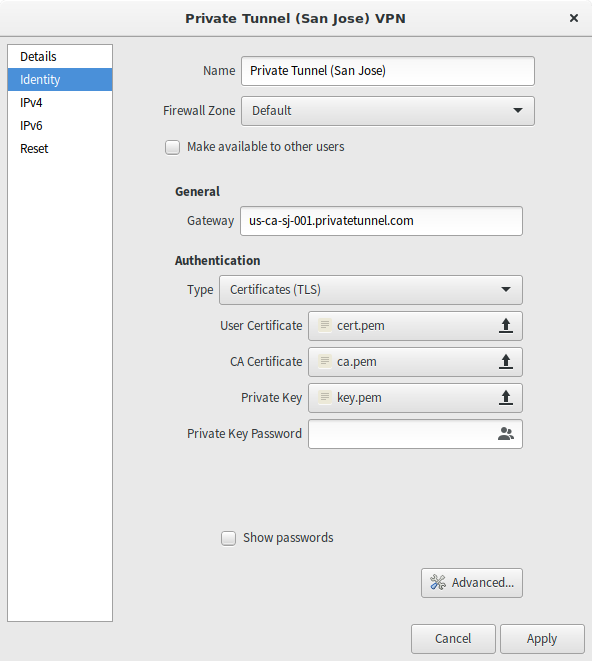
Configure endpoint, certificates.
After setting the endpoint (remote in .ovpn file above) and
selecting the certificates clck "Advanced..."
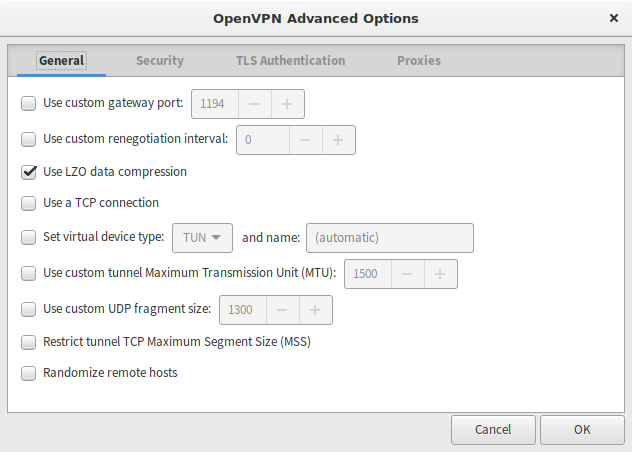
OpenVPN Advanced Options - General
Select "Use LZO"
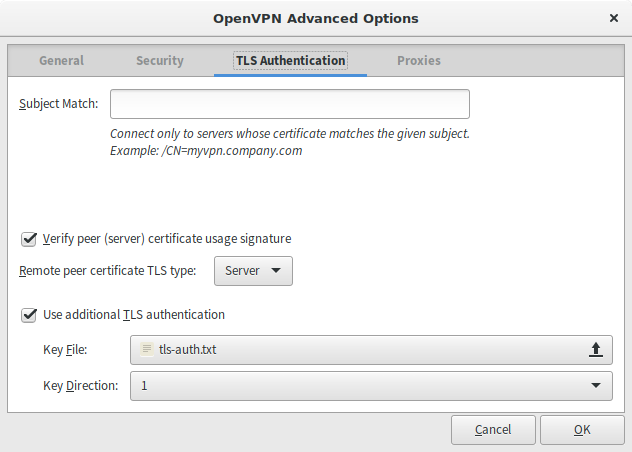
OpenVPN TLS Authentication
Verify Peer - remote is Server, set the path to tls-auth you
created before and select "1" as key direction.
Now, Private Tunnel has posted their Network Manager guide detailing
these steps, and they also want you to patch the openvpn script, but
according to OpenVPN Community Wiki this is no longer needed,
as --remote-cert-tls option passed by NetworkManager is the
proper one.
Here's the cool part - based on my experience, all the certificates and keys are the same across all Private Tunnel endpoint, so if you want to connect to a different location, you only need to change the endpoint address.
As always, logs may help you to figure out what's wrong: